The Cyber Security Awareness Ideas
Table of ContentsCyber Security Awareness Can Be Fun For AnyoneCyber Security Awareness for BeginnersSome Ideas on Cyber Security Awareness You Should KnowGetting The Cyber Security Awareness To Work
An IT professional may suggest disconnecting an unpatched medical gadget from the network (sequester) till it can be covered, whereas the professional engineering expert would certainly consider the risk vs. advantage of leaving the unpatched gadget on the network as well as going after one more mitigation approach till the medical device can be covered.The first one of these was the MDS2 (HIMSS MDS2, 2017) which has a lengthy listing of details regarding clinical gadgets safety and security qualities. Much more sophisticated as well as semiautomated CE-focused cybersecurity products are under growth that scan a hospital's network in real-time and also combine that information with MDS2s, CMMS information, cyber threat databases, and gadget manufacturer web sites to produce a cybersecurity-focused view of the HDO's gadget landscape (Asimily, 2017).
Information is vital in your day-to-day procedure, and also data loss prevention approaches ensure your data is offered for your gain access to in all times. Not simply any person in your business ought to have accessibility to the company's delicate info. Gain access to and identification management makes sure data is accessed just on a need-to-know basis which those getting the information are who they say they are.
measures required to secure a computer or computer system (as on the web) versus unapproved accessibility or assault 1989, in the significance specified above Last Updated: 9 Sep 2022 Subscribe to America's largest thesaurus and get thousands extra meanings as well as progressed searchad totally free!
Cyber Security Awareness Can Be Fun For Everyone
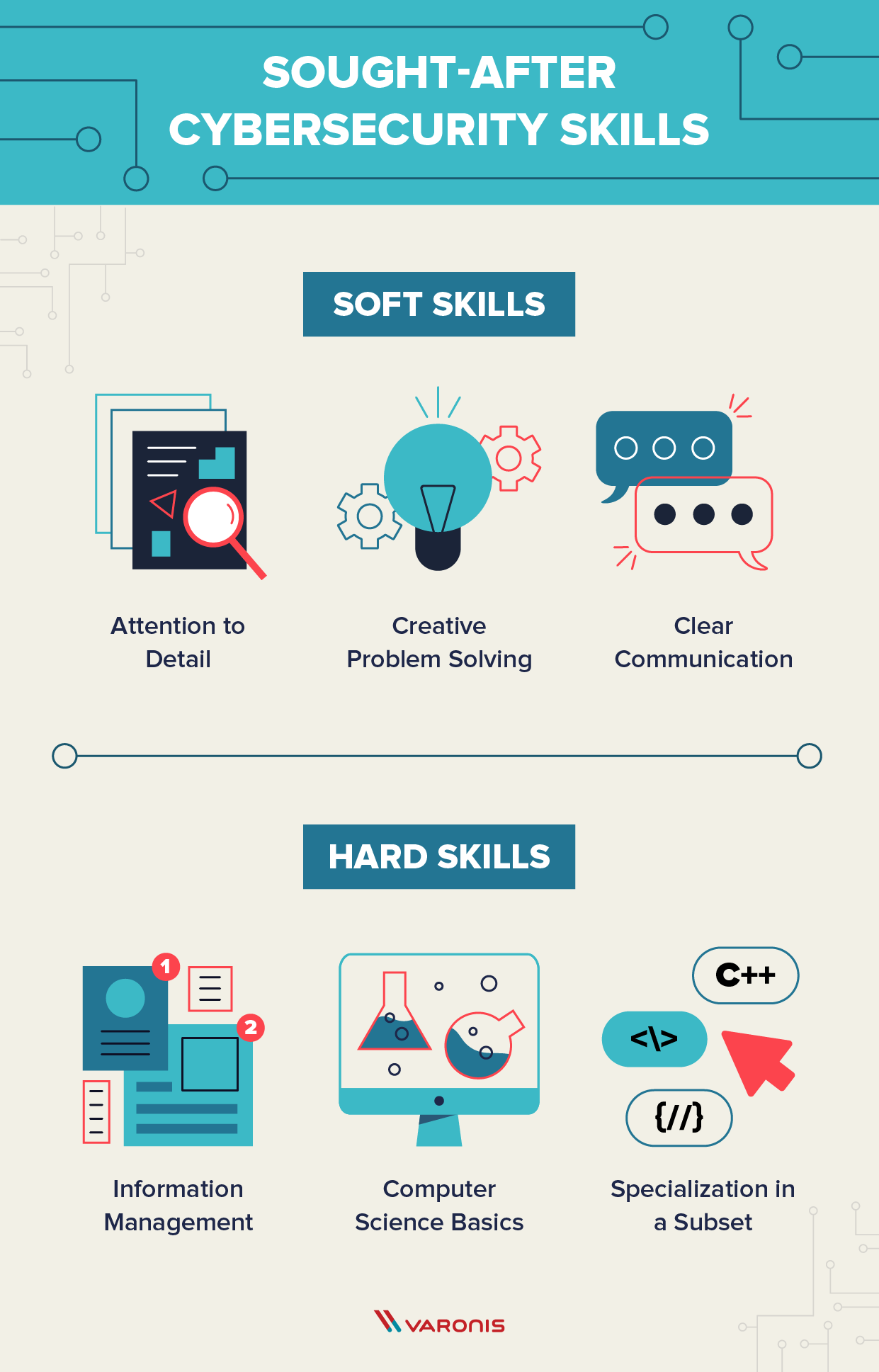
New Zealand requires to be able to depend on a solid cybersecurity workforce that's capable of stopping, adjusting to, and replying to cybersecurity risks. This programme is created to furnish you with the core cybersecurity and technical skills and expertise you require to shield and also take care of information and systems security.
For Research, Web link functions please guarantee your application states your earliest training course beginning day. For this programme, you will certainly require the following: Have actually successfully completed 120 credit scores of a level 5 IT credentials or over or comparable expertise, abilities and experience Approval to Unitec carrying out a Cops clearance check, or a Criminal Document Inspect, and also suggest Unitec of any kind of present fees or pending court issues A minimum of 8 credit scores at NCEA degree 2 in English (4 in Reading, 4 in Writing), If English is not your initial language, you are required to have one or more of the following: Have actually achieved NCEA Degree 2 and also New Zealand College entrance Be able to supply evidence you please our standards for existing English effectiveness Have actually achieved at least one get redirected here English proficiency end result in the last 2 years For more information on the training courses consisting of timetables, please click the course names listed below.
0 credit scores (0. 125 EFTS) This program will enable student to study, evaluate, choose as well as apply read this a series of tools and also methods to create a solution to a cybersecurity problem. Wherever, feasible students ought to execute a job in behalf of a client. 15. 0 credit reports (0. 125 EFTS) This program will certainly make it possible for trainee to research study, evaluate, select and also apply a variety of tools and also techniques to establish a service to a cybersecurity issue.
The info had right here is correct at the time of posting, however as the programme evaluation is continuous, the courses detailed might be liable to alter with time - Cyber Security Awareness. Feel confident that we will inform you of any material adjustments to shipment that might impact what you research study, where you study or the methods you learn.
Excitement About Cyber Security Awareness

The cyber risks of today are not the very same as even a few years ago. As the cyber hazard landscape modifications, here companies need security versus cybercriminals' current and future devices and also techniques. The cyber protection threat landscape is constantly evolving, as well as, periodically, these improvements represent a new generation of cyber hazards.
While collaborations as well as supplier connections benefit service, third-party users and software must have gain access to limited to the minimum necessary to do their tasks and should be continuously kept track of. While ransomware has actually been around for years, it only came to be the leading kind of malware within the last few years.
Excitement About Cyber Security Awareness
Over the last few years, phishing attacks have only expanded more sophisticated. While the original phishing scams were relatively very easy to spot, modern attacks are persuading and also advanced to the factor where they can be essentially equivalent from legit emails. Employee cyber safety and security understanding training is insufficient to safeguard against the contemporary phishing danger.

Malware strikes were much less typical as well as less innovative, as well as company facilities were much less intricate. Today, cyber safety and security teams are often overwhelmed while attempting to manage these complicated cyber safety styles. This is created by a number of aspects, consisting of: Modern cyberattacks can no much longer be identified with tradition methods to cyber protection.
As on-site employees. Trying to solve all of these challenges with a range of disconnected solutions is unscalable and unsustainable.